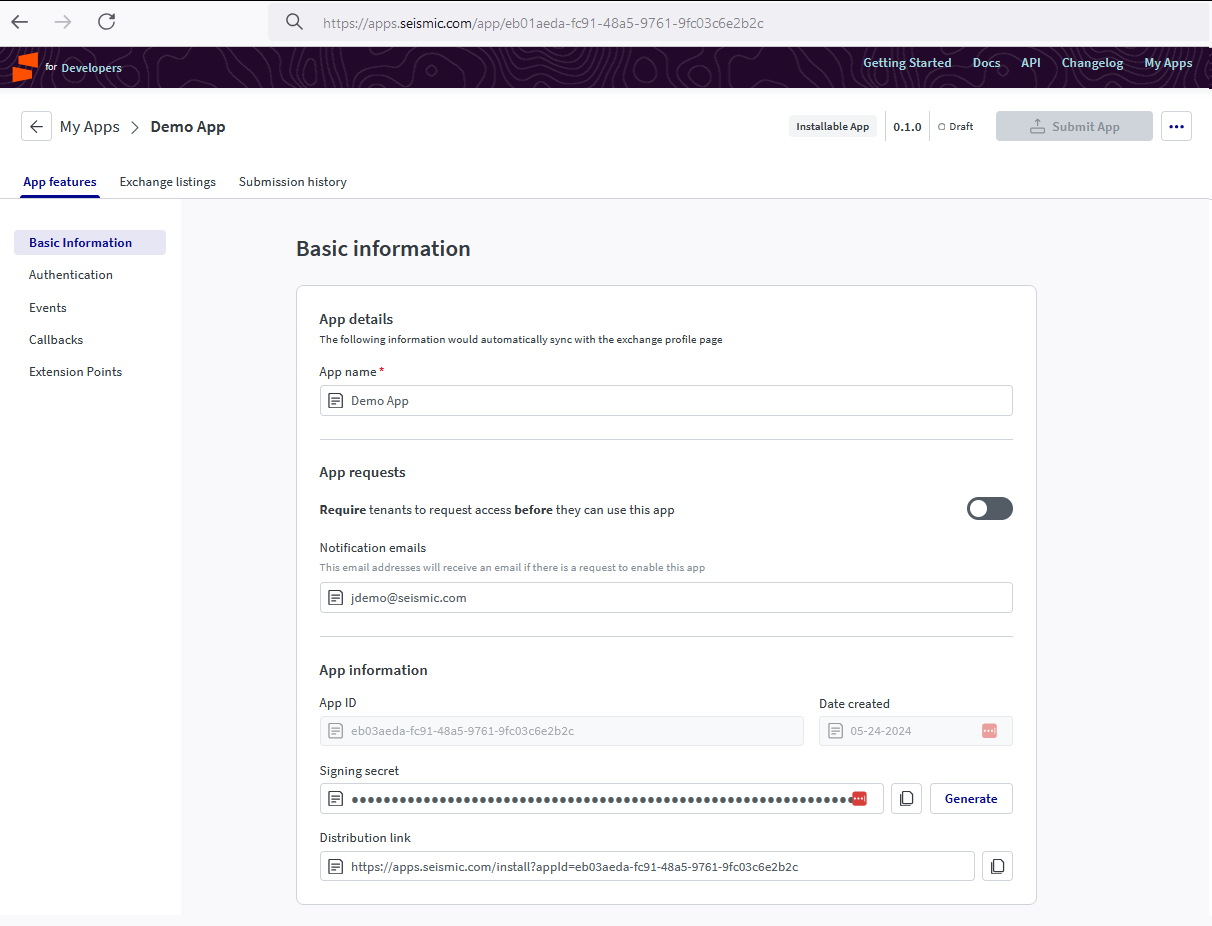
Basic information
Basic Information
Use this section to define the application metadata. This data is used to enrich the experience of the Seismic admin who will ultimately be configuring your application. All information entered in this section will be visible within the Manage Apps page.
Required fields
While only app name is required, we strongly encourage that all apps populate as much information as possible to enrich the experience of the Seismic admin. Failure to populate certain fields may deter users from installing/enabling the application.
| Field | Description |
|---|---|
| App name (Required) | The name of your app. |
| Notification emails | List of comma separated email ids where you intend to receive app related notifications. (Optional) |
| App requests | Allows you control which tenants can enable your app. (Optional) |
App information
| Field | Description |
|---|---|
| App ID | The unique ID for this application. This ID will not change |
| Date Created | The datestamp of when this app was created |
| Signing Secret | A generated key that can be used to validate requests and payloads. Read more below. |
| Distribution Link | Share this URL with a tenant admin to give them the ability to install your app in their tenant. You can read more on App Distribution |
Signing secret
App registration supports the generation of a signing secret that can be used to validate payloads that originated from Seismic.
All applications that want to receive callbacks (install, uninstall, enable, disable and update) or use the Configuration UI extension will need to generate a signing secret because Seismic uses this secret to sign payloads. We will use this to encrypt the JSON payload we post to you. You can then ensure that the calls are in fact coming from Seismic.
The signature is calculated using a HMAC algorithm using SHA265. The signature is sent with each request in the request header. The header key for the HMAC is x-seismic-signature.
The recipient service should use the secret to validate that the payload HMAC using SHA256 and compare it with the x-seismic-signature sent in the request header. This same approach can also be used by external services (like content uploader) to send requests to Seismic using the extensions platform.
The secret is issued to an app and is not tenant specific.
Signing secret regeneration
If the signing secret is leaked, it can be regenerated in App Registration. The signing secret is common for all versions of the app - published and unpublished.
Updated over 1 year ago