The client credentials with user delegation flow may be used by highly-trusted server-to-server applications to provide active authentication. This flow is also known as user Delegation flow.
In this authorization flow, the app installer within a particular Seismic tenant consents a particular user to be the sole delegated user. The delegated user is the user that will be used to retrieve access tokens, and is the user that should be considered as the actor for any actions taken by the app.
Unlike the authorization_code and implicit flows, this authentication flow does not redirect users to a login page. It authenticates a user, predetermined by the tenant admin, with a single request. This flow should only be used by trusted server-to-server applications.
You should use this flow only if using a redirect-based flow is not possible. If this is not the case and redirects are possible in your application, you should use the authorization_code or implicit flow instead.
How to guide
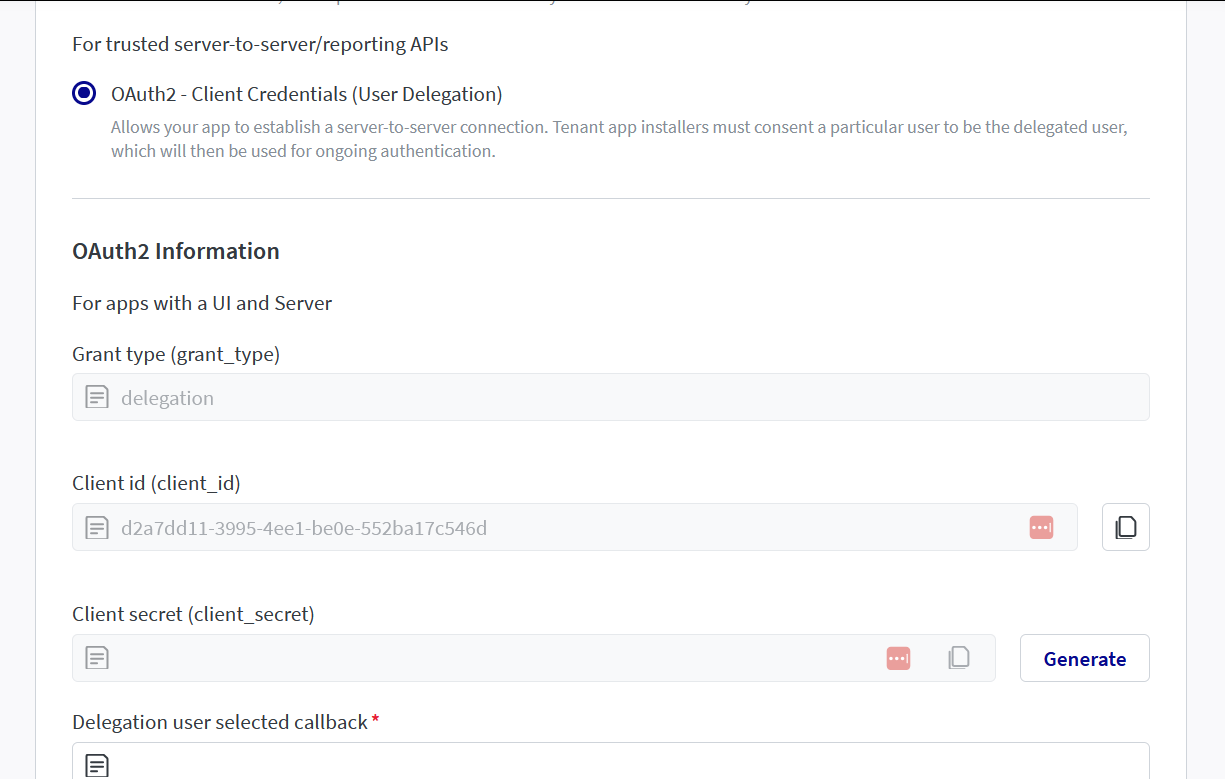
Create an app with User Delegation Flow
- Create an app on App Registration Portal.
- Select authentication method as Client Credentials.
- Add your user delegation callback url. The delegated user id will be sent to this url.
- Generate the client_secret from the app.
Setting the delegated user from your Seismic UI
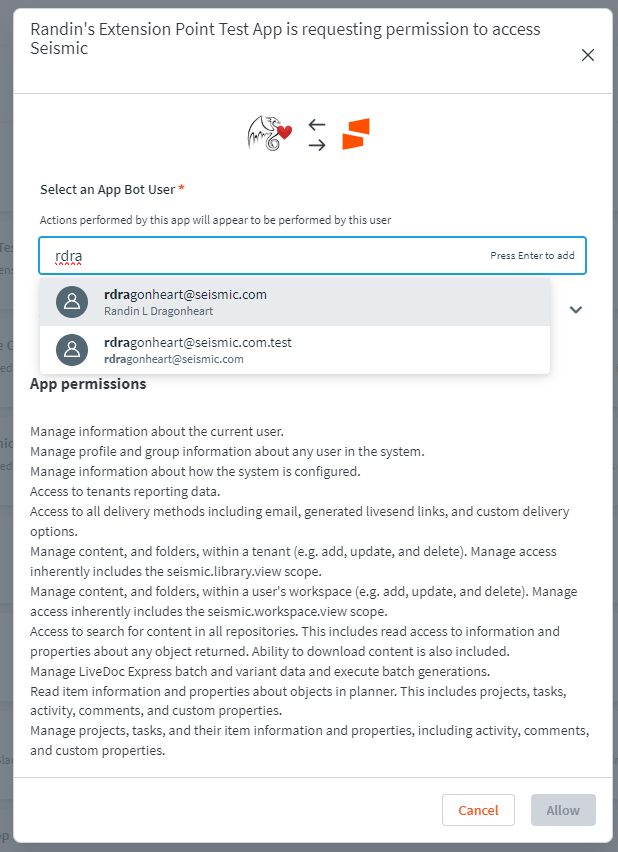
When an administrator enables an app within a tenant they are presented with a window that asks them to select a user. Enabling an app is handled in Settings > System Settings > Manage Apps > My Apps by the toggle switch. The user that is selected here is the Delegated User and the only user that can authenticate into this app in this tenant.
Storing delegated user credentials for the client credentials flow
When a user is selected during the App Enable process Seismic will send a payload to the URL that is in your Delegation user selected callback field from within in your Apps Authentication > OAuth 2 configuration.
Each time the delegated user for an app is added/changed by a tenant admin, Seismic will post the following payload:
POST /api/v1/applications/zenDesk/config HTTP/1.1
x-seismic-signature: 3548541BF3C6431018DABB6BEAE815158A565843C60F38CFE6894514F3B49A2B
Content-Type: application/json
Accept: */*
Cache-Control: no-cache
Host: localhost:5580
Connection: keep-alive
Content-Length: 296
{
"userId": "1", // this is the admin user who set the delegation user
"userEmail": "[email protected]", // this is the admin user who set the delegation user
"delegationUserId": "b48d244c-1cce-4e6b-aad9-7e6820a99hh7", //the ID of the selected delegation user
"appId": "fcdd244c-1cce-4e6b-aad9-7e6820a99a20",
"appName": "ZendeskTest",
"tenant": "intdev2",
"tenantId": "b061ad37-1f5a-4531-b7d3-89807dccca68",
"requestId": "8709b156-b0d2-45fe-a43c-8aff052af56f",
"version": "0.1.1",
"language":"en-US",
"timestamp": "2020-09-08T14:55:06Z"
}
Your system must store the delegationUserId returned in this payload. It will be needed to retrieve access tokens for this user from within this tenant. Please refer to 1. Get a token using client credentials for retrieving your Bearer Tokens.
Token lifetime
- Access token expiration: 21600 seconds (6 hours)