This step initiates the OAuth 2.0 Authorization Code flow using PKCE (Proof Key for Code Exchange).
PKCE is required for public clients such as browser-based apps, mobile apps, or desktop applications.:
Prerequisites
Before starting, ensure you have the ability to generate cryptographically secure random values for code_verifier and code_challenge.
code_verifier(random)code_challenge = BASE64(SHA256(code_verifier))
For testing
Use these values for testing on this page. These are test vectors provided on https://datatracker.ietf.org/doc/html/rfc7636#appendix-B
code_verifier=dBjftJeZ4CVP-mB92K27uhbUJU1p1r_wW1gFWFOEjXk
code_challenge=E9Melhoa2OwvFrEMTJguCHaoeK1t8URWbuGJSstw-cM
code_challenge_method=S256
Initiate the OAuth:
https://auth.seismic.com/tenants/<your tenant>/connect/authorize?
response_type=code&
client_id=<your client id>&
redirect_uri=<your redirect URL>&
scope=<scopes space separated>&
state=<your opaque value>&
code_challenge={code_challenge}&
code_challenge_method=S256
Refreshing tokens
Add
offline_accessscope in OAuth url if your application needs to refresh the token.
Parameters
response_type: Must be code
client_id: The client_id for your authorization_code client app provided by Seismic.
redirect_uri: The URL to which Seismic will redirect the browser after authorization has been granted by the user. The Authorization Code will be available in the code URL parameter.
scope: The scopes which you want to request authorization for. These must be separated by a space. You can request any scopes which your application has access to. Be sure to include offline_access if you would like to get a long-term Refresh Token.
state: An opaque value the application adds to the initial request that Seismic includes when redirecting back to the application. This value must be used by the application to prevent CSRF attacks, click here to learn more.
code_challenge: SHA-256 hash of the code_verifier. It should be Base64 URL-encoded.
code_challenge_method: Must be S256
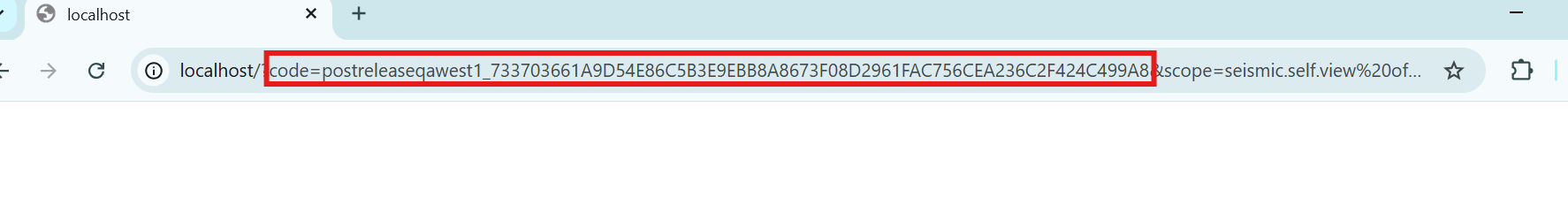
Response
The Authorization code will be appended to the redirect url.